In this lesson, I am going to do the basic things that you can do using the firewall filters on Juniper. Let me show you what scenario I have here:
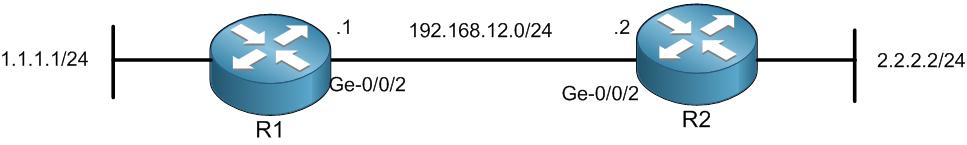
This is my scenario, R1 and R2 are connected to each other and IP addresses are already set. I have also the static route set so 1.1.1.1 can ping 2.2.2.2 and vice versa. Let me show you this:
root@R1# run ping 2.2.2.2 source 1.1.1.1
PING 2.2.2.2 (2.2.2.2): 56 data bytes
64 bytes from 2.2.2.2: icmp_seq=0 ttl=64 time=3.822 ms
64 bytes from 2.2.2.2: icmp_seq=1 ttl=64 time=5.349 ms
64 bytes from 2.2.2.2: icmp_seq=2 ttl=64 time=6.910 ms
64 bytes from 2.2.2.2: icmp_seq=3 ttl=64 time=3.782 ms
^C
— 2.2.2.2 ping statistics —
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max/stddev = 3.782/4.966/6.910/1.288 ms
[edit]
root@R1#
root@R2> ping 1.1.1.1 source 2.2.2.2
PING 1.1.1.1 (1.1.1.1): 56 data bytes
64 bytes from 1.1.1.1: icmp_seq=0 ttl=64 time=3.502 ms
64 bytes from 1.1.1.1: icmp_seq=1 ttl=64 time=6.510 ms
64 bytes from 1.1.1.1: icmp_seq=2 ttl=64 time=5.207 ms
64 bytes from 1.1.1.1: icmp_seq=3 ttl=64 time=7.064 ms
^C
— 1.1.1.1 ping statistics —
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max/stddev = 3.502/5.571/7.064/1.371 ms
root@R2>
Excellent, they can ping each other.
I want now to disallow R2 to ping 1.1.1.1 while allowing him to ping any other IP address. Also I want R2 to keep a logging when the filter rule is being matched.
Let me show you how you can do that:
root@R2# edit firewall filter ICMP-BLOCK term TERM1
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2# set from protocol icmp
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2# set from destination-address 1.1.1.1/32
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2# set then discard
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2# set then log
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2# show
from {
destination-address {
1.1.1.1/32;
}
protocol icmp;
}
then {
log;
discard;
}
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2#
I have created a filter rule that in case the destination is 1.1.1.1/32 and the protocol is ICMP, then it will be blocked and will have a log file.
However, keeping the filter rule like this only will discard any other traffic because on Juniper there is a hidden implicit deny rule which deny everything else. So I should create a Term 2 and allow everything else, you got me?
Let me show you how you can do that:
[edit firewall filter ICMP-BLOCK term TERM1]
root@R2# up
[edit firewall filter ICMP-BLOCK]
root@R2# edit term TERM2
[edit firewall filter ICMP-BLOCK term TERM2]
root@R2# set then accept
[edit firewall filter ICMP-BLOCK term TERM2]
root@R2#
Let’s see how the firewall filter looks now completely and if it is good I will save it:
[edit firewall filter ICMP-BLOCK term TERM2]
root@R2# up
[edit firewall filter ICMP-BLOCK]
root@R2# show
term TERM1 {
from {
destination-address {
1.1.1.1/32;
}
protocol icmp;
}
then {
log;
discard;
}
}
term TERM2 {
then accept;
}
[edit firewall filter ICMP-BLOCK]
root@R2# commit
commit complete
[edit firewall filter ICMP-BLOCK]
root@R2#
Excellent, this is what I want to see.
Now the filter rule is created but we have to apply it.
We should apply it on the outbound of the interface of G-0/0/2 interface because the traffic is leaving R2 on its interface Ge-0/0/2 to R1 in order to reach 1.1.1.1
Let’s do it:
root@R2# edit interfaces ge-0/0/2 unit 0 family inet
[edit interfaces ge-0/0/2 unit 0 family inet]
root@R2# set filter output ICMP-BLOCK
[edit interfaces ge-0/0/2 unit 0 family inet]
root@R2# commit
commit complete
[edit interfaces ge-0/0/2 unit 0 family inet]
root@R2#
This way, I have configured the filter rule on the right interface in the way out.
Let’s check now if 2.2.2.2 can still ping 1.1.1.1.
root@R2> ping 1.1.1.1 source 2.2.2.2
PING 1.1.1.1 (1.1.1.1): 56 data bytes
ping: sendto: Operation not permitted
ping: sendto: Operation not permitted
ping: sendto: Operation not permitted
ping: sendto: Operation not permitted
ping: sendto: Operation not permitted
^C
— 1.1.1.1 ping statistics —
5 packets transmitted, 0 packets received, 100% packet loss
root@R2>
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments