Contrary to the transit traffic, exception traffics are traffics that are going to the Juniper device itself and terminating there. Some examples include:
- Ping to the Juniper router
- Telnet to the Juniper router
- SSH to the Juniper router
- Routing updates
The question that is asked, where those traffics are arriving at? Is it the Forwarding plane or Control plane?
In that case, the exception traffic enters first from the Juniper interface to the Forwarding plane because that’s where the interface is connected to, then Packet forwarding engine will check that this is not a transit traffic but an exception traffic. So, what it does, it will send it via the Internal link to the Routing Engine in the control plane.
Let me show you that with an illustration:
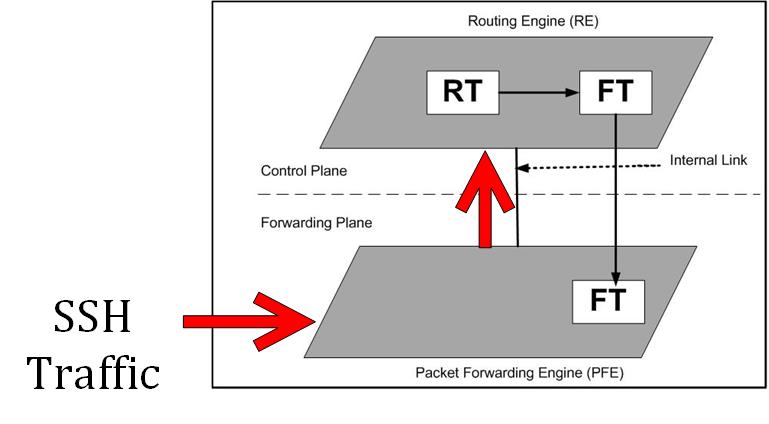
The SSH traffic goes to the ingress interface, the Packet forwarding engine in the Forwarding plane finds that it is not a transit traffic then it will send it over to the Routing Engine via the Internal link.
You may say then that this is a nice way by the hacker to issue their attacks by targeting the Routing Engine with DDOS (Distributed Denial of Service Attack). That is somehow true but the beauty on Juniper device is that the Internal Link has a rate limit which is NOT CONFIGURABLE by an administrator, and it has some limitation on the rate that the internal link can have between the packet forwarding engine and the routing engine (and vice versa). This will reduce the severity of the DDOS on the Juniper router.
This is all what I wanted to explain to you in this chapter, I hope you enjoyed it and see you in the upcoming one.

0 Comments