Now I have to discuss about Firewall Raw. Something you may have seen when you go to IP/Firewall on MikroTik:
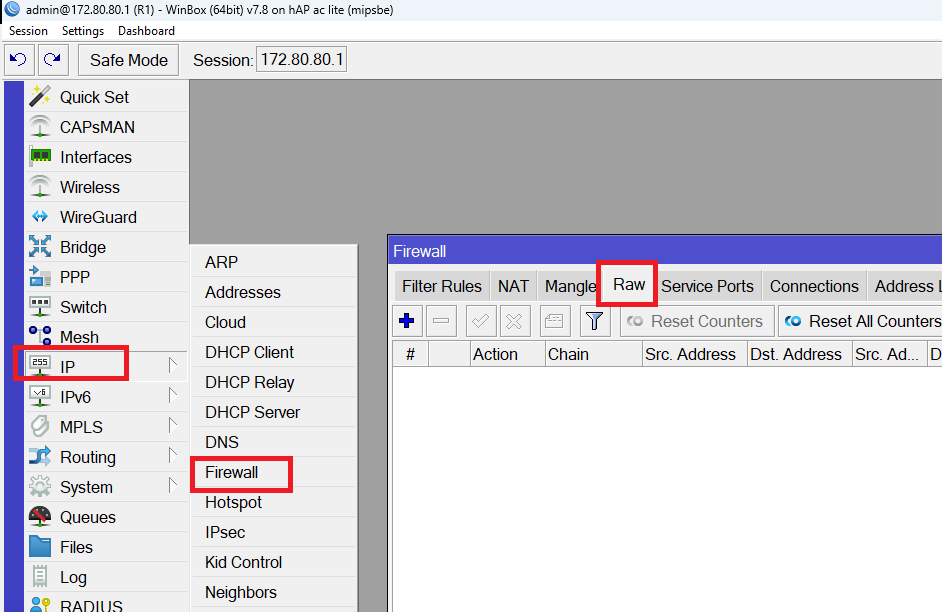
The question that may come to your mind: What is the Firewall Raw and what differs from the Firewall Filter Rules that we have been discussing about it in the whole book.
Well, the answer is as follows: Firewall Raw can do filtering on packets reaching the MikroTik RouterOS device before it reaches the connection tracking. As we have seen before, the MikroTik RouterOS is a stateful firewall which keeps tracking on all connections passing, which is something very good. But the problem here is that in case you have a DOS attack like TCP Syn attack, then the MikroTik RouterOS will keep in its connection tracking table all those entries issued from that attack causing the router CPU to go to 100% (something we have seen it when we were speaking in this book about the TCP Syn attack).
To avoid this, you can apply your firewall rules against the TCP Syn attack on the Firewall Raw, this way the router will drop the TCP syn attack packets before they reach to the connection tracking, and this would help that our router keeps having a better CPU performance. However, I should mention that the firewall itself consumes as well a lot of resources from the CPU, that’s why I always advise that you implement a big MikroTik devices as a firewall which can have many core CPU’s and a large memory (preferably a RouterOS image installed on a server blade).
The other question that you may ask: how did we decide that Firewall Raw works before the connection reaches the connection tracking?
Well here, we can go to the subprocesses of the routing box in the packet flow diagram and we can so the following:
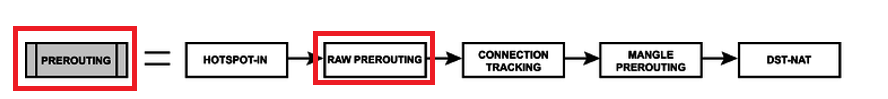

We do have 2 chains where we can apply Firewall Raw rules:
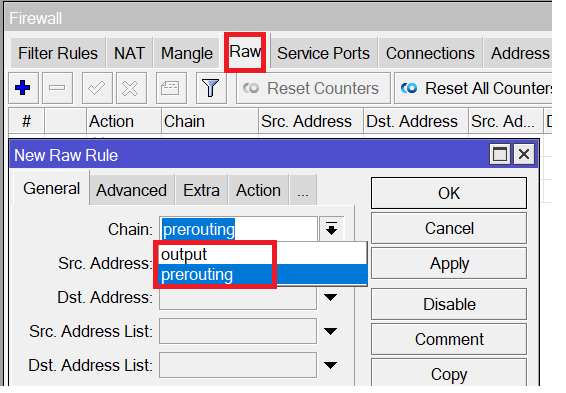
- Prerouting chain
- Output chain
And that’s something I can show it clearly on Winbox when I open a Raw rule, you can see we do have only 2 possibilities to use as chains: Prerouting and Output:
If you look carefully at each of the chains, you see that Raw always comes before the connection tracking. That’s why we can drop packets on the Firewall Raw before they reach the connection tracking and exhaust our MikroTik router.
Now we know the theory, let’s apply a LAB to see how we can protect our MikroTik router from TCP Syn attack but this time using the Firewall Raw.
LAB: Firewall RAW against TCP Syn Attack

Back to the scenario where the attacker is sitting on the internet and wishes to issue a syn flood attack against our MikroTik router. I am not going to explain again about this type of attack because I have already done this previously in this book. Also, we already know that if the attacker issues the syn flood attack, then the CPU of the MikroTik router goes to 100% and we will have a huge list of TCP entries in the connection tracking (something we have seen previously).
Let’s focus now by working on the firewall raw rules to protect from this type of attack:
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments