Attackers use port scan attack to determine which ports on your router or on the network are open and available. By running a port scan attack on a router or on a network, the attacker will know which ports are open and are listening to information. Also, he can know what version the application is using. All this would help the attacker to use port scan as a “gate” for starting an attack and penetrating our network.
We have already seen port scan before in this book when we were using NMAP to discover which ports are open on the MikroTik router. This is exactly what port scan is.
Let’s directly do a LAB to see how port scan attack runs and how we can protect against it.
LAB: Port Scan Attack and Prevention

I am still having the same scenario. The attacker is on the internet and he is willing to do a port scan to our router which has a public IP.
With the help of NMAP on Kali Linux, a port scan can happen as the following:
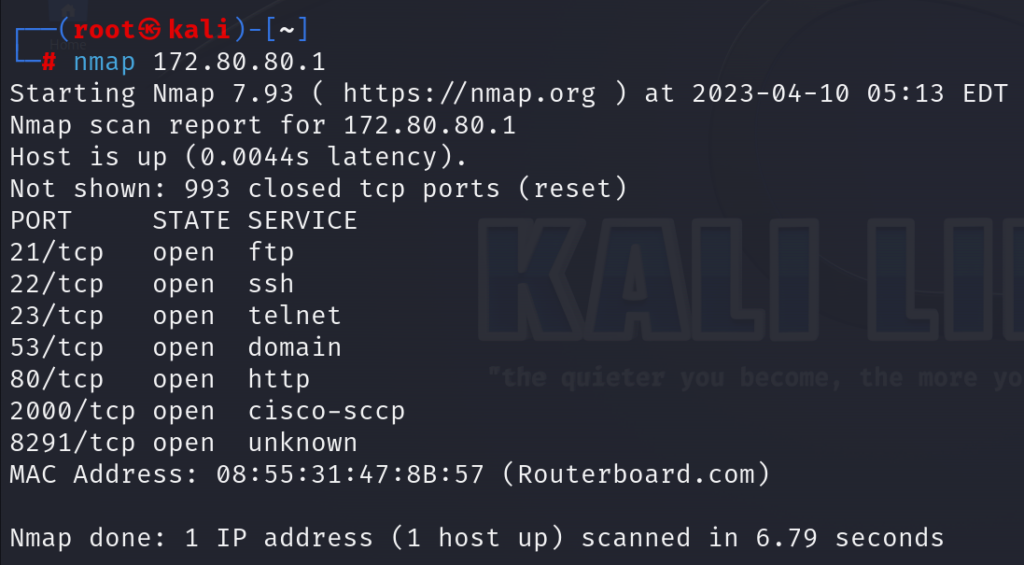
You can see, the port scan attack is working on my MikroTik router.
Now we need to disallow the port scan to happen. To do that, we have to think of the logic – where does port scan happen normally?
Well, it can happen to the MikroTik router itself, or it can happen to the devices inside my network, meaning that the port scan attack hits the router trying to guess its ports that they are open, or will pass via the router to go to the inside devices to guess the open ports on those devices.
Meaning that I must disable port scan as the following:
- To the router (hint: chain input).
- Via the router (hint: chain forward).
Let’s start with the 1st rule. In this rule, I will have to detect if there is a port scan attack happening to the router, and if yes then the IP of the source issuing this attack will go to an address list. The rule which will come directly after it, will be to just drop any IP which is the address list from the 1st rule.
Let me show you that:
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments