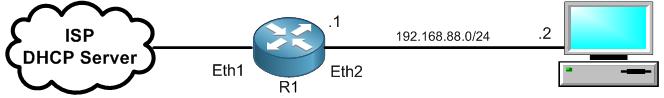
In this LAB, I will show you how you can secure your MikroTik router using the connections states. At this moment, I am on the LAB scenario where R1 is connected to the internet and sharing internet to my PC.
What are the connection states? There are 5 different connection states in the MikroTik firewall that you can use.
Those connection states are:
- New
- Established
- Related
- Invalid
- Untracked
The most important ones are the first 4.
Let’s speak about each one of them:
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments