ICMP is a very important protocol that we use in the network. It can be used to do troubleshooting or possibly to give us a message when something happens to the link as an example.
However, attackers may use this protocol to crash our network devices because ICMP does not require any type of authentication to run. For this reason, we have to know what type of ICMP messages we should keep enabled and what we should disable.
You may ask yourself now: does ICMP have many types? Well, the answer is yes ????
Ping request is an ICMP type, Ping reply is another ICMP type, traceroute is another ICMP type, and the list can continue.
I have taken this picture from IANA website to show you how many types do ICMP have:
(https://www.iana.org/assignments/icmp-parameters/icmp=parameters.xhtml#icmp-parameters-types)
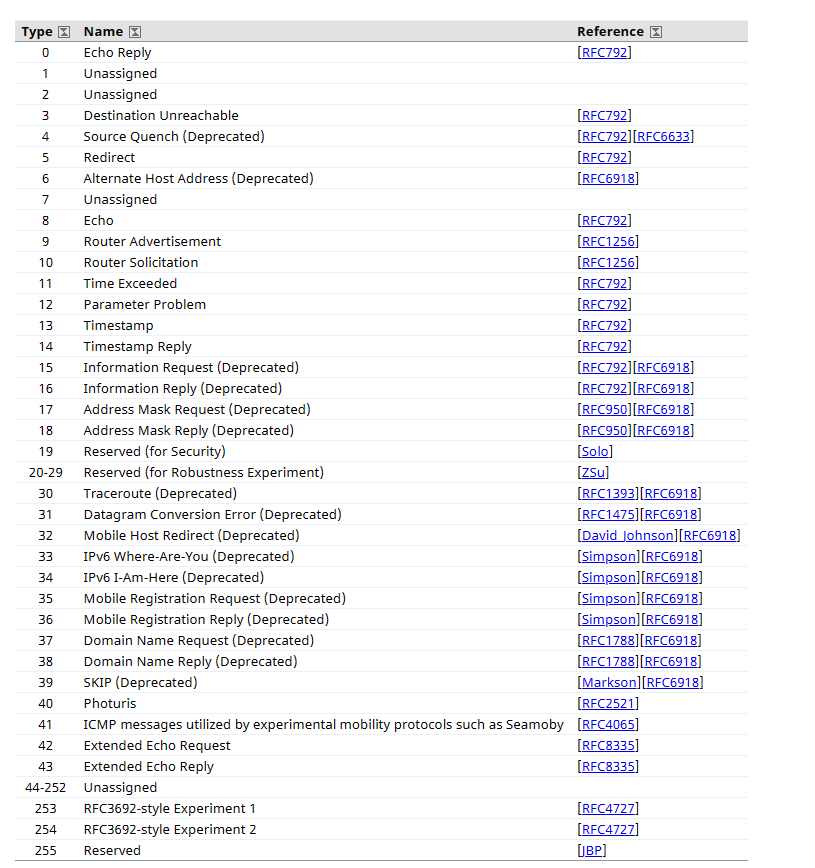
Moreover, on each of those listed ICMP types, there are codes. For example, ICMP type 0 has only 1 code which is code 0:
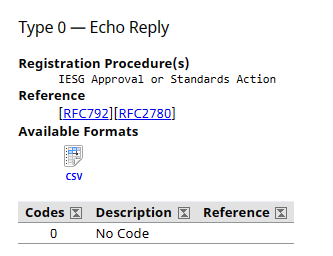
With this I know that ICMP type 0 code 0 is for Echo Reply. Based on that, I will use this information to allow or disallow this type of ICMP.
While ICMP type 3 and many codes as you can see below.
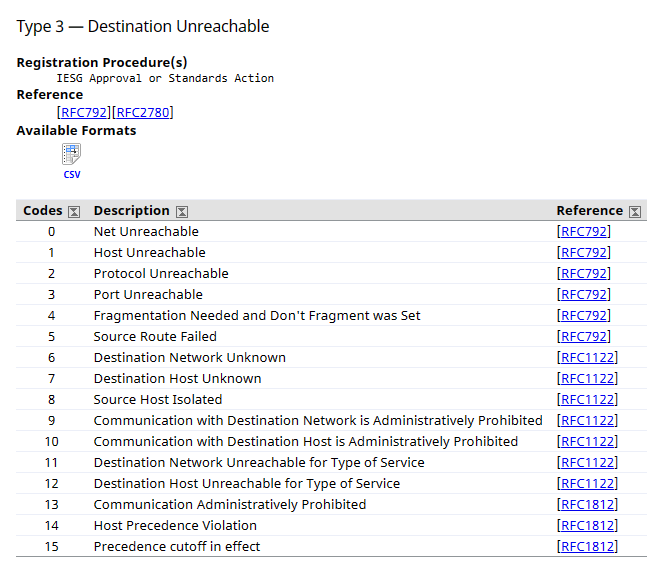
Each combination of types and codes refer to a specific ICMP message.
Now we understand that ICMP has many types, and each type may have many codes, let’s apply on a LAB and only allow the ICMP types that we wish to run in our network.
LAB: ICMP Filtering
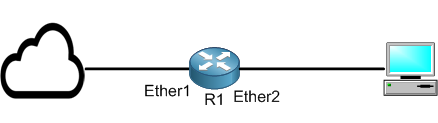
I am on this scenario now; my PC is connected to R1 on Ether2 and has from it an IP address of 172.80.80.254/24.
To check, let’s issue a ping from the PC to R1:
It is working perfectly ????
The mission of this LAB is to allow the following 3 ICMP types to pass:
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments