When we were speaking about the packet flow diagram, we have seen that there is a firewall inside the bridging box, meaning that we can do firewall on the Layer 2. That’s what is called “Bridge Filter”.
This can be seen clearly on Winbox when you go to the Bridge:
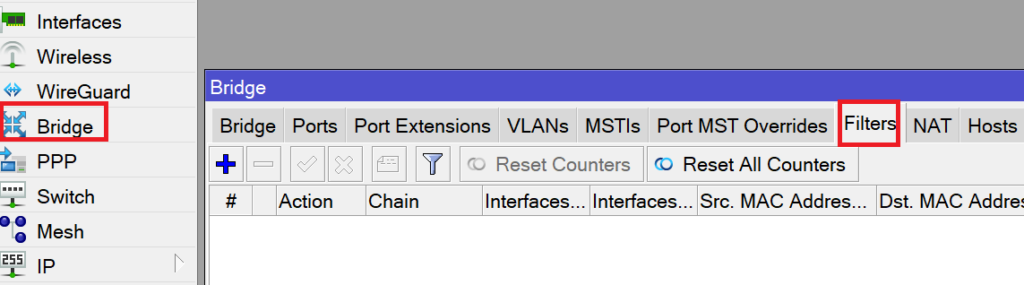
The question that may ask. What can we do in the bridge filter? Maybe to answer to this question is to make a LAB showing how you can use bridge filter.
LAB: Bridge Filter to Prevent DHCP Rogue
By now, you should already know about the DHCP Rogue attack that an attacker can do (I have explained this with a complete LAB in this book).
Just as a reminder, DHCP Rogue attacks is when an attacker plugs on our network a DHCP Server to lease IPs to the internal devices (as well the gateway address) then he can intercept all traffic that those internal devices will be doing.
I will show you how you can forbid this to happen by using the bridge filter feature we have on Layer 2.
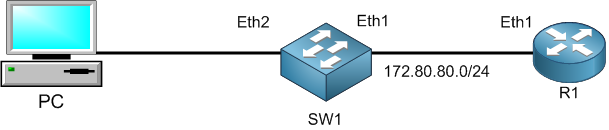
As you see in the graph, R1 is acting as a router with DHCP server enabled, we do have a switch (SW1) acting as a switch in which I have created a bridge port and put inside of it the interfaces Ether1, Ether2 and Ether3 to be bridged together.
IMPORTANT NOTE: please be aware, whenever you need to use the switch bridge filter, the ports that you will be adding in the bridge should not have hardware offload enabled. If you have hardware offload enabled, then the traffic will not go to the router CPU hence the bridge filter will not work.
Let me show you that the 3 interfaces (Ether1, Ether2 and Ether3) have the hardware offload unchecked:
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments