MNDP means MikroTik Neighbor Discovery Protocol, is a protocol that allows us to find neighbor routers/switches which are compatible with the following neighboring protocols:
- MNDP: MikroTik Proprietary
- CDP: Cisco Proprietary
- LLDP: Open Standard
All you need to do is to have a device physically connected to the your device so it will be discovered using any of the above 3 protocols (if all are enabled on the MikroTik router). Please note that the MNDP runs on UDP Port 5678.
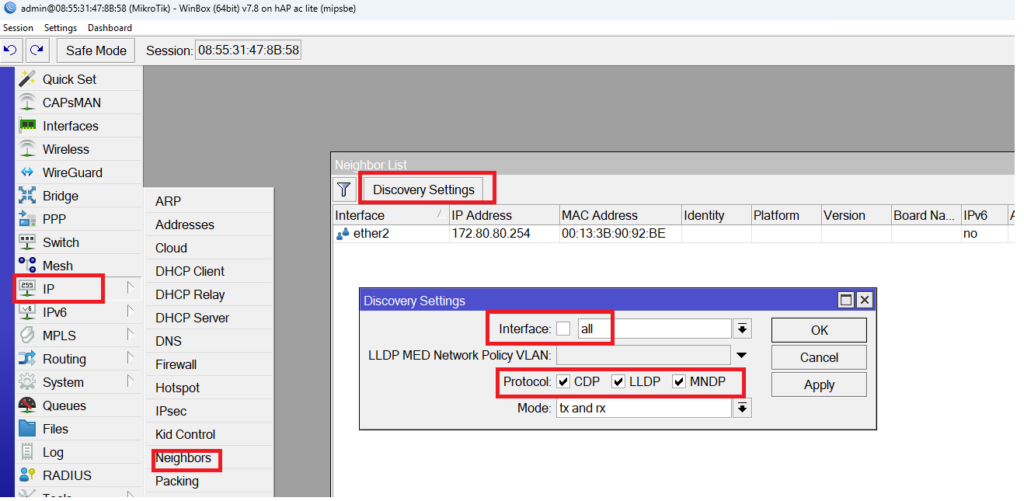
I have here a MikroTik router running on RouterOS v7, and if you go to IP/Neighbors, you can see that all 3 neighbor discovery protocols are enabled on all interfaces, also you will see that it has already discovered on its interface Ether2 a device with an IP of 172.80.80.254 and MAC address of 00:13:3B:90:92:BE.
Also, those protocols help us to see the MikroTik router entry on Winbox when we open it on our PC as the following:

That’s indeed an advantage, but there are also some disadvantages. The main disadvantage is that, in case an attacker run an attack on the CDP protocols, he can make a huge list of entries as neighbors for this router, and this would cause the router CPU to go to 100% and not being operation anymore.
Let me show you a LAB about this directly.
LAB: MNDP Attacks
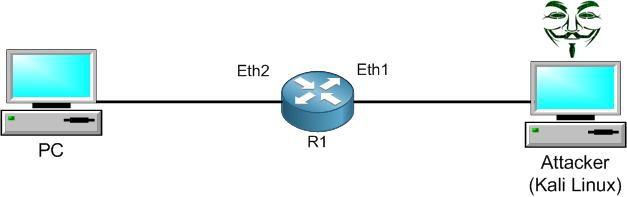
This is my LAB setup. I have prepared a Kali Linux machine (normally used by attackers) to launch an MNDP attack to R1, and I have connected it to Ether1 interface. What Kali Linux will do is to send many thousands of neighborship entries to R1 from different MAC addresses, so R1 will believe that he has all those entries as real neighbor devices to him. In a result, the CPU of the router will go to 100% and it won’t be able to run the normal task that a router should do.
First, I will run the attack, then I will show you how to fix it.

From Kali Linux command prompt, I will open the software called “yersinia” as a graphical user interface to make the neighbor attack.
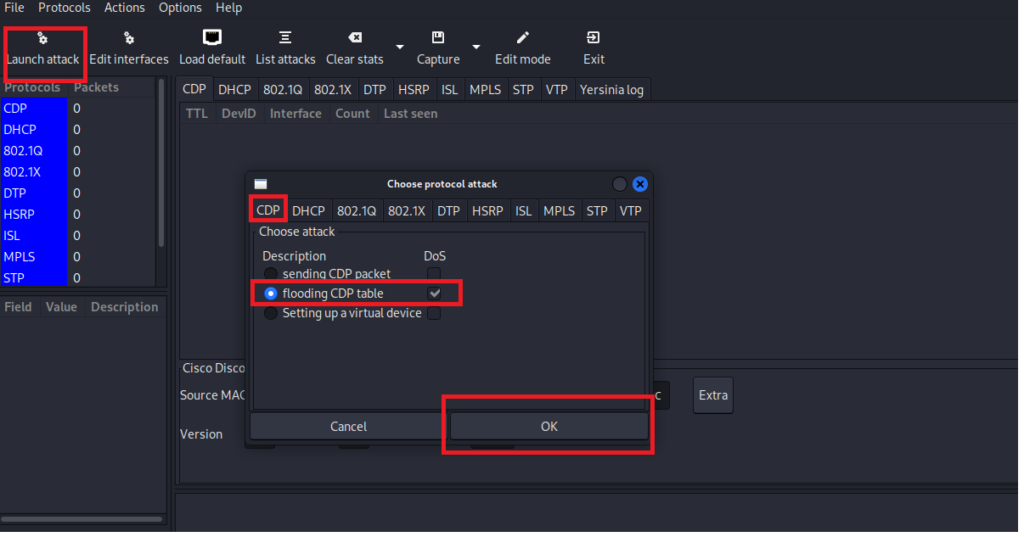
To run the CDP attack from Yersinia, all you need to do is to launch the attack and choose “flooding CDP table”. I have already started the attack, so let’s see what is happening on the MikroTik router.
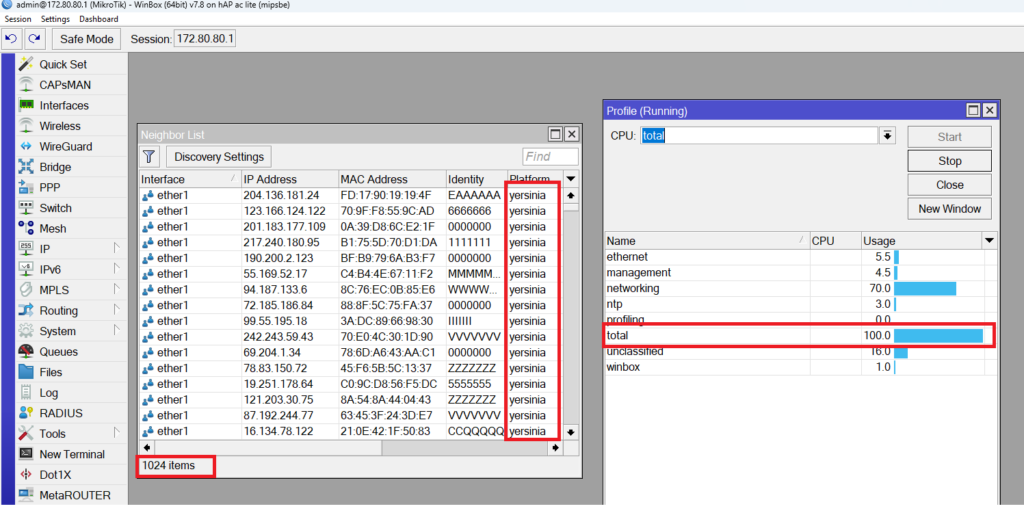
Wow!!!! Look how many entries have been added on the router neighbor list, and look at the CPU – it is already 100%.
That’s not good at all, and now anyone with Kali Linux machine running Yersinia may cause a huge damage for our network.
Now we have seen how the attack will happen, let’s see how to mitigate it.
The only way to mitigate this problem is to select which interface(s) on the MikroTik router need to have MNDP/CDP/LLDP protocols enabled on it. Let’s really think about it for a minute: do we really need to have the WAN interface having neighborship discovered? What about the interfaces which are un-used, do we also need to have the neighbor discovery protocols enabled on them?
In our scenario, we want Ether2 to keep having the neighbor discover protocols enabled on it, but on Ether1 (which is connected to Kali Linux) we do not want that.
So what we can do, we can use the “interface-list” option and then apply the one we want on the neighbor discovery.
Let me show you how to do this:
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments