We are still discussing different types of attacks that we may encounter on our MikroTik router, and another attack that I would like to discuss about it is called: Password Brute Force Attack.
The goal of this attack is to obtain credentials information such as a password from the device that the attacker is attacking (in our case the MikroTik router). As you know, to login to the MikroTik router we always require putting a username and a password whether on Winbox, Telnet, SSH, Console, etc….
If the attacker can guess the admin password that we have on our router, then he will gain full control of the router and exploit many techniques to profit from having access to that router.
Brute force attack is an automated software that generates a large number of consecutive guesses and combination of letters, numbers, symbols, characters in order to guess the password of the device that is trying to find its password.
For this reason, I highly advise you to always change the username of the router (other than “admin”) and make a very complex password to make it hard for the attacker to guess it.
Let’s do now a LAB to see how the Brute force attack happens and how to mitigate it.
LAB: Password Brute Force Attack and Prevention

Still on the same LAB scenario, R1 is connected to the internet and has SSH enabled so the administrator can login to the router via SSH remotely.
The hacker will profit from this by running a brute force attack on the SSH port 22, in order to be able to guess the password.
At this moment, the username and password on my router are:
Username: admin
Password: 123456
Let me show you, in case you are using a simple password, how easy it is for the attacker to guess your password.
I will go to Kali Linux and run Hydra graphical to run the brute force attack against R1:
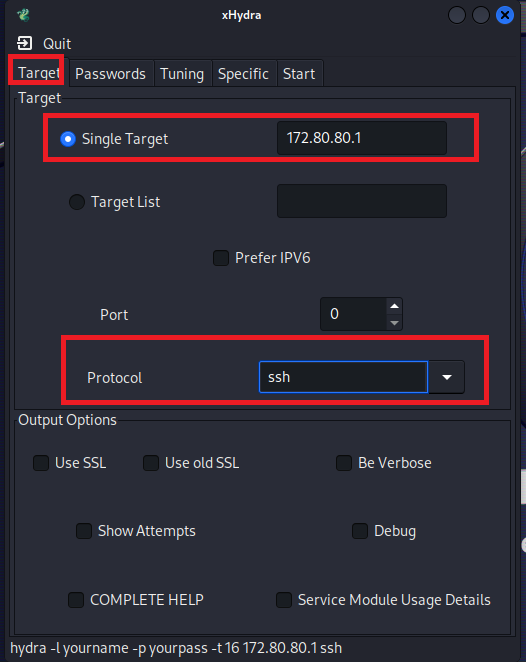
I have said to Hydra that I want to run the attack on the router which has the IP 172.80.80.1 and on the protocol ssh.
Now I should mention how to guess the username and password:
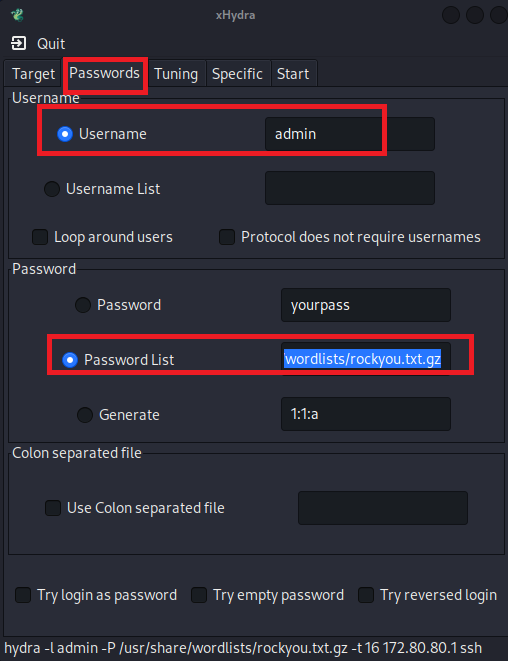
For the username, I want that all tries to use the username “admin” because I believe that most of network engineers leave the username the same on the MikroTik router, and for the password I want to use the different combination of password that are available in the file list called “rockyou.txt.gz” (this file comes inside Kali Linux and contains thousands of passwords that hydra can use for the brute force attack).
Now that I am ready, let’s start the attack:
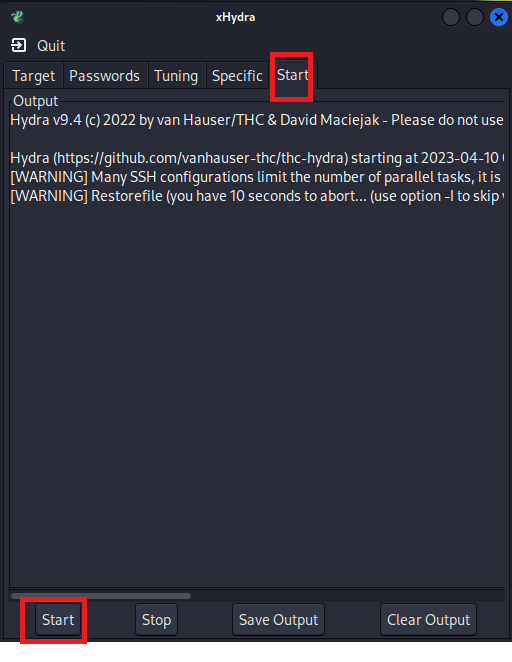
The attack has started, and now I see in front of me that hydra could, in less than 5 seconds, guess the router password which is “123456”:
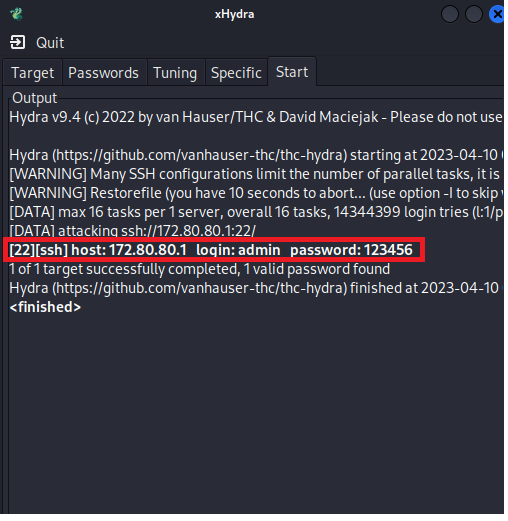
Oh my God! Imagine with just simple steps we could guess the router password. When I look to the router log, I see that it took him 5 tries to guess the password:
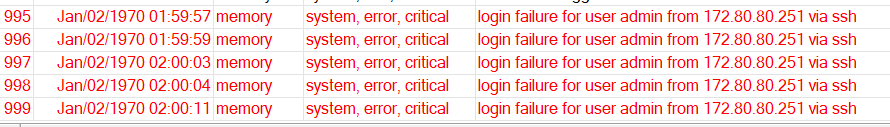
Now you know how the attack happens, let’s see how we can protect our MikroTik router from such types of attacks.
Before we speak about the filter rules, you should do some settings on the router to make things harder for the attacker to guess your credentials. I will list some of them:
- Always use a very complex password and change the admin username to something else.
- Periodically change your password.
- Disable protocol that you never use them to log into the router (like Telnet, http, FTP, etc…..).
- Change the default ports of the protocols used to login to the router. For example, change the ssh port from port 22 to another port like 2222.
- Deploy port knocking (we will speak about it later in this book).
- Apply filter rules to limit the number of times a user can unsuccessfully attempt to log in and lock the users who exceed the specified number of failed login attempts.
Now let’s do the mitigation – I will start creating the filter rules to protect from Brute force attacks.
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments