Once you use the network command on OSPF advertising a network, then hello packets are sent out of the interface where this network belongs to in order to try forming neighborship with a peer router.
But what if we have the following scenario?
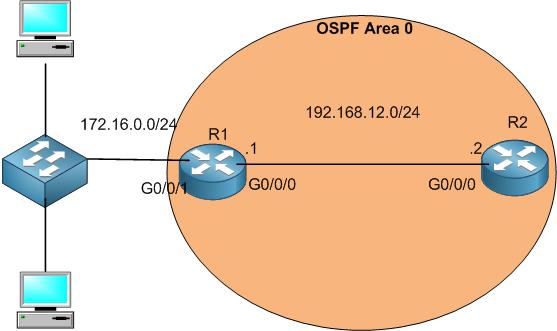
In this scenario, you need to advertise the connected networks on R1 into OSPF so R2 can know about R1 networks, that means the following 2 networks will be advertised on OSPF on R1:
- 192.168.12.0/24
- 17216.0.0/24
Once you advertise those 2 networks, hello packets will be sent out of the 2 interfaces as the following:
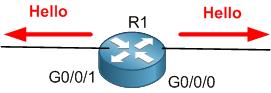
Of course, we need the hello packets to go via the interface G0/0/0 so R1 can form OSPF peer neighborship with R2, but do we really need that the hello packets go out via G0/0/1 which is connected to a LAN switch? Of course not, and this is actually a security hole because someone can emulate OSPF on his PC then he can form neighborship with R1 and he can run attacks to our network. But at the same time, R1 should advertise the network 172.16.0.0/24 which is connected to the interface G0/0/1 to allow R2 to know about it. So, what is the solution here.
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments