In the last part of this chapter, you need to know how to secure the MikroTik Switch Access. There are different things you can do to harden your MikroTik Switch so you do not allow anyone to access the switch. For this you require to do many steps to harden the switch as follows:
- Use a different username from admin and put a new password, then delete the default admin username.
- Allow only some IPs to login to the Switch. Those IPs should be for the administrators. This can be done from here:
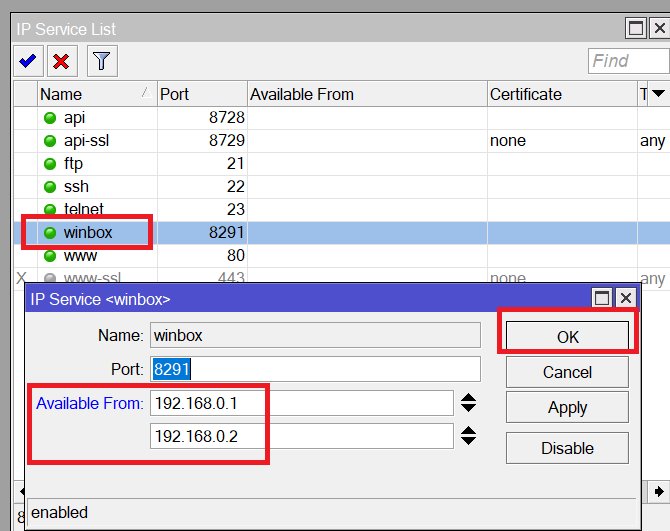
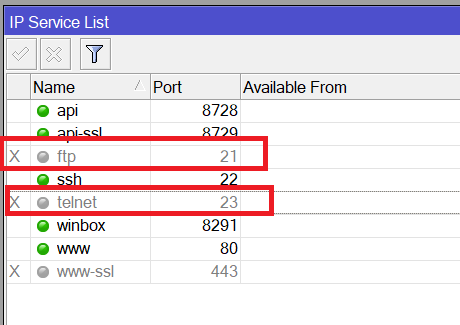
- Disable unsecure services that a hacker may use to access your switch such as Telnet and FTP.
Apologies, the Full Lesson Access is Only for Members....

Get Access to all Lessons from different Vendors
Affordable Price to Enhance your IT Skills!
Always Accessing all Lessons including the New Added Ones

100% Satisfaction Guaranteed!
You can cancel your membership at anytime.
No Questions Asked Whatsover!

0 Comments